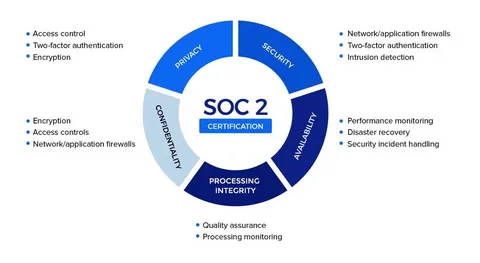
Regarding security and data privacy, a SOC-2 report is the most common so far that you usually refer to accepting the standard data privacy controls. In addition, a SOC 2 certification provides an auxiliary layer of security and confidence with your clients or partners. Most of the service providers in organizations such as financial services, health care units and government agreements follow SOC 2 audits, even if they are unnecessary.
How to implement for best SOC 2 Compliance?
It is essential to determine the scope of the audit. Every business or organization contract does not demand to comply with the standard of confidence.
If you do not understand the scope or requirements of an audit, your organization may waste valuable time and resources that do not require confirmation.
Before being audit, you need to understand your technical infrastructure. If, for example, you are not using construction software, you will need to upgrade naturally. If you are using a third-party platform or SaaS product, you will need to comply. A SOC 2 certification provides an auxiliary layer of security and confidence with your clients or partners.
However, you may never need SOC2 confirmation. For example, a healthcare IT company has to meet HIPAA’s needs and can be enough. Despite hospitals or insurance companies such as covered companies (CES), a SOC audit must ensure additional scrutiny of your security system.
The same case for a financial services company that handles payment information. Although they can meet PCI DSS requirements, they can also choose to undergo SOC2 audit for extra reputation.
How can an adviser help you prepare and complete the SOC 2 audit?

There is a need for a lot of additional exceptional work to prepare and complete the SOC 2 audit that the Chief Information Security Officer (CISO) and his team need. However, for the first time, learning to learn the SOC 2 certification for first time to complete this task, and some grow companies have been known to get the SOC 2 certification.
A lot is capable of doing current executive leadership, such as a CTO. The problem in this perspective is that it takes time to assign them to these tasks of cybersecurity and compliance that they can spend on the leading role of their highest value.
It is why many companies turn to Virtual CISO consultants to help them prepare and fulfil their SOC 2 audit. Virtual CISO is experienced with SOC 2 and can benefit from each step from the initial scope to the audit.
Model of SOC 2 compliance;

Here is a miniature model of SOC2 audit works that helps Virtual CISO.
Perform a Gap Assessment: A gap assessment is determining for taking a survey of an existing cybersecurity program and finding the difference that needs correction to get your company audit-ready.
Getting technical controls and implementation – if there are no efficient technical controls, advisers help companies add these desired controls to improve security and ensure compliance.
Adjust the policies and procedures– as to the above protocol, policies and practices are not possible to audit unless they try to do so.
Make content effective– the content will be critical documents for the SOC2 audit. They can write policies, procedures, and reports and get them in their place.
Manage Project – Virtual CISOs are experience and can manage the audit project. Domain expert project managers say something.
Perform risk assessments – Risk assessment is essential to complying with SOC2, and a virtual CISO can perform an evaluation and write the report.
Vendor Management – Vendor management is essential for every SOC 2 compliance program. However, if it will not be available in an organization, it may be valuable to outsource an expert.
Perform “External Internal Audit” – Internal audits help ensure that your company does everything needed before the auditor catches you. The external auditor knows the standards and can keep the organization accountable.
Choose an Auditor – A good Virtual CISO is experience and knows to practice a good SOC 2 and can remove auditor selection from your plate.
Advocate on your behalf with the Auditor – Your virtual CISO will advocate for you, ensuring that the auditor will set expectations for your organization for realistic compliance.